SSL Decryption with Palo Alto NGFW
Palo Alto Networks Firewall v8.0.4
SSL Decryption Policy
This walk-through assumes you have an internal CA server in your production environment (e.g. Microsoft).
1. Go to the Device Tab->Certficates. Lets import our CA certificate from the Microsoft Internal CA Server (e.g. http://x.x.x.x/certsrv). Click "Download a CA certificate, certificate chain, or CRL", choose Base64 and click "Download CA Certificate". Save this to an accessible location (e.g. Desktop) so it can be imported into the PAN-FW.
2. Back in the PAN GUI, import the CA cert and give it a comprehensive name (Note: You would click "Shared" if configuring this via Panorama and if you would like this cert to be used by multiple device/s. In this instance, we are configuring on a single local Firewall). Click ok!
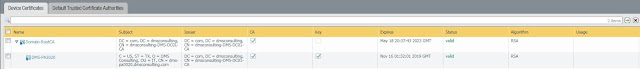
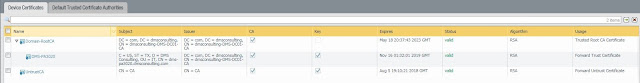
Note: Click on the new Domain-RootCA cert, put a check mark next to "Trusted CA" and click ok! You will now see this reflected under the "Usage" column for the Domain-RootCA cert.
3. Now, lets create a CSR to be signed by the internal CA. Click on Generate, fill in the details as applicable to your environment
4. Again, click generate. You will now see this certificate in a "pending" status. Click to check the cert, then click export. Save the CSR to an accessible area such as the desktop. Open the file with an editor (e.g. Notepad), copy the entire contents.
5. Now back to the Internal CA Server, click "Request a certificate", then click on "advanced certificate request". Now paste the contents of the CSR, ensure the "Certificate Template" field is "Subordinate Certificate Authority" and click submit. Check the "Base 64 encoded" and click "Download certificate", save to Desktop
6. Back to the PAN Firewall, click the checkbox for the pending cert and click Import. Give the certificate a comprehensive name (Recommended this be the same name as the cert), browse to the signed CSR and click "Ok". The cert is now uploaded and ready!
7. Now we need to ensure the new cert is used as a forward trust certificate. Click on the new cert, put a check mark next to "Forward Trust Certificate"
Note: Forward Trust Certificate: The firewall uses this certificate to sign a copy of the server certificate that the firewall presents to clients during SSL Forwarding Proxy decryption when the certificate authority (CA) that signed the server certificate IS in the trusted CA list on the firewall.
8. Now we need to create a Forward "Untrust" Certificate. Click "Generate" and create a simple self-signed certificate as shown. Once created, click the cert and put a check mark in the "Forward Untrust Certificate" field.
Note: Forward Untrust Certificate: The firewall uses this certificate to sign a copy of the server certificate the firewall presents to clients during SSL Forward Proxy decryption when the CA that signed the server certificate is NOT in the trusted CA list on the firewall.
9. We have now created all the certificates needed to support SSL Decryption. The Device Certificates tab should now look as follows
10. Lets create a Decryption Profile, go to the Objects Tab->Decryption Profile, click Add. Give the profile a comprehensive name. On the SSL Forward proxy tab, lets check "Block sessions with expired certificates" and "Block sessions with untrusted issuers". We will leave the rest default, click ok!
11. Now we need to create our policies, companies typically take some time to discern what traffic they wish to decrypt and that which they will not subject to decryption. It is a typical approach to NOT decrypt traffic such as Financial Services (e.g. Online banking), Shopping Services (e.g. Amazon, PayPal), Health Care Services (e.g. Cigna, BCBS). Now once the "No-Decrypt" policy has been defined and signed off by the business, we then create another policy that will then subject all other traffic to decryption/inspection.
Click Add - Lets create a new Decryption Policy. From left to right, fill in the appropriate details per your environment on the General, Source, Destination, Service/URL Category, Options tabs. On the options tab, we will select our previously created Decryption Profile.
I have created a typical set of SSL Decryption policies as shown below
12. Save and Commit changes to the firewall
13. SSL Decryption has now been configured and is ready to be tested
Note: We will use the "Monitor" tab to view traffic, respond to any issues that may arise from traffic now being subjected to SSL Decryption
Let's quickly test SSL Decryption:
I have done some general web browsing, we can now see this in the Traffic logs under the Monitor tab. Click the magnify glass next to the log entry, notice the checked flag?
That traffic flow has been decrypted, inspected and sent on to its destination and I happily browsed the webpage with no issues and closed it once I was done!!!
I am using Chrome for this testing. As you now browse to secure sites, you can now verify that the PAN Firewall is officially playing the Man-In-The-Middle role - Go to Options->More Tools->Developer Options->Security Tab and now view the certificate. Do you see who has issued the certificate for that secure traffic flow?
Some helpful CLI Commands:
This command will show you existing SSL Decryption sessions that are being handled by the NGFW
> debug dataplane pool statistics | match Proxy
This command will show you how many active sessions have been decrypted
> show session all filter ssl-decrypt yes state active
That my friends is SSL Decryption leveraging the Palo Alto NGFW!
Happy Decrypting and until next time...keep it secure and flowing.......!













Hi,
ReplyDeleteThis is very good article. I am configuring exactly the same thing in my environment. Just one question regarding the "Certificate Template" and that is why do we need to select "Subordinate Certificate Authority" in the "Certificate Template" field ? Why it is mandatory to select that option?